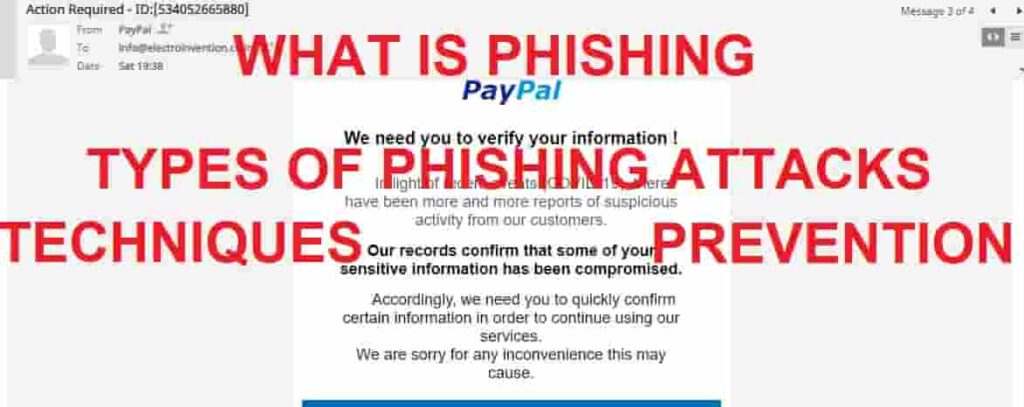
Phishing – What is Phishing? and how to prevent it and be safe. What is the meaning of phishing and the different ways you can get phished? Hello everyone and in this article, I am going to elaborate a little bit on Phishing. So let’s first know what is phishing?
Phishing is a type of cybercriminal activity in order to gain access to other people’s(target or targets) crucial data or information through the means of electronic communication. It is a kind of fraud in which the target/ victim’s all sensitive data is tried to access in an unauthorized way by mimicking the identity of a trustworthy organization. Phishing is one of the most common techniques used by intruders to gain access to your crucial and sensitive data.
Phishing attacks can be through Emails, Messaging, text messaging or social media links posting as legit institutions, and where users are asked to input sensitive information such as PINs, OTPs for transactions, adding Credit Cards, etc.
This information can then be used for purposes like Identity theft, information stealing, or unauthorized access to the bank balance. Users are scammed through communications claiming to be from trusted parties like banks, social media websites, lottery,etc.
Sometimes there can also be a case of the victims being directed to a scam websites that look legit like looking brand or organization or something on social media or Email like, “To Play this game, Sign-in with Facebook or Google account”. or
“Hi, this is an email from your XYZ bank, we are updating our database. So Please, log in with your internet banking ID so that we can verify you.” several other ways we are going to discuss ahead in this article.
Below are some of the different types of Phishing attacks and different techniques used in them are explained.
At the END OF THE ARTICLE, I am going to reveal about a recent Phishing Mail attack on Us! and how did I had detected that the mail is a SCAM in the name of an International Brand.
Phishing attacks types
1.Spear Phishing:- Usually, in most of the phishing techniques, it’s generally a large mass of people recipients or victims who are sent attacks. But, Spear Phishing is something that is specifically targeted. An individual or targetted individual from an organization is sent attacks. An intruder or hacker applies this by pretending to know you well.
In most cases, there is commonly a commercial/ business Email to the target’s Inbox. Usually, in this case, the cybercriminal shoots a mail pretending to be a senior employee or the authority panel of that organization. The attacker now tries to convince them and connect them by impersonating the people you know. Like colleagues or other staff members. This they can do by gathering info. about you from your internet activity, data breaches and also collecting data from your contacts using P2P protocols. This is where social engineering comes into play.
For Example, You’re Michael, and you work for Bryan, who’s the CEO of the company. Now, Mr.Bryan had to go out of station for some emergency. The hacker came to know that by your boss’s Facebook updates. Now, the hacker creates a fake email address from your CEO’s name, for eg. bryanramyofficial@gmail.com, and with his fake digital signature that looks similar. He now emails you requesting an immediate wire fund transfer on the CEO’s name from the company to an account abroad. As shown in the snip below.
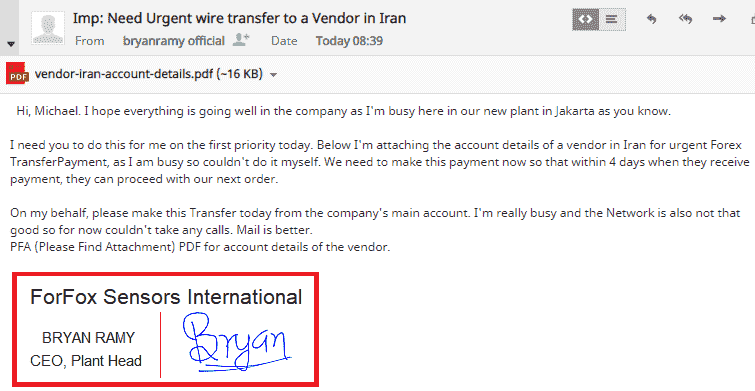
So this was a very simple example for spear phishing. In this, technique for phishing by email is used. Now let’s move to other types.
2.Whaling:– Whaling is an even more targeted type of phishing. It is basically spear phishing attacks that are aiming at the senior-level employees of an organization or institution. In this case, the email content is created for Managerial or senior-level roles. In this case, normal malicious links or fake signatures aren’t useful. As for the senior staff, it is like ‘ Phishing(Fishing) a bigger Fish.
Usually, tax return forms are the common kinds of ways. Or the account data verification scam, filing of ITR Refund, PayPal account details verification, mew SaaS platforms demo scams(Try this SAP Software or something like that). All of these are usually common types.
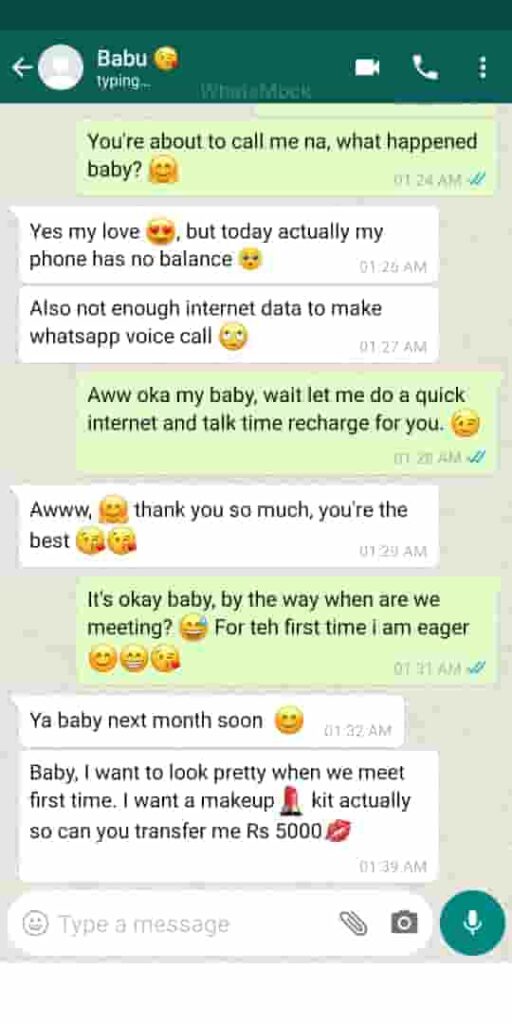
3.Catphishing and Catfishing: Catphishing or Catfishing both are similar kinds of online deception activities that involve getting close to a person through online communication especially social media, in order t gain access to information and resources of the target. Whereas, the only difference is Catfishing is a bit more closely. In this, a person creates fake social media accounts with a dishonest purpose to get someone into a romantic relationship and also making fake promises of love and real life. The main goal of the perpetrator is to get money and resources of the target or to receive other benefits like gifts, etc. This is something they do through social media or chatting as well as dating apps.
for eg. see the demo image below, is a handmade chat but a very good example of catfishing.
4.Clone Phishing: Clone phishing is a type of phishing when a scammer/ hacker replicates exact copy of an email previously delivered by a legitimate and authentic source. The only thing which is changed is placing some malicious links instead of the original links.
By using link manipulation technique these links too are shown as to be legit original and legit, but in fact they’re originally pointing to an infected site.
For example, the link here shows to be pointing at HDFC bank, But, in reality, when you’ll click it, it will take you to the homepage of Electroinvention.co.in.
Link: https://www.hdfcbank.com/
5.Voice Phishing: It is also called as Vishing. Not all kind of phishing requires fake email, malicious websites, etc. In this case, it’s by spoofing a phone number from a legitimate source and then requesting PINs, OTPs, or ask for crucial and sensitive information pretending to be from legitimate organizations. For eng. calling by VOIP. Voice over IP.
6.SMS Phishing: SMS Phishing or SMISHING is phishing over SMS messages. These are usually done using text messages over phone numbers on large scales mostly. They usually ask you to fill and register yourself to some fake baits, click a link, call a number, etc. The victim is then invited to provide their private data, often, credentials to other websites or services.
Techniques involved in different types of Phishing
1.Link Manipulation: Mostly in phishing attacks, they use some kind of deception technique for making the link to look like it’s from a legit source but in fact it’s going somewhere else. Use of similar subdomains and misspelled URLs , usually when you click them they take you to something similar or a property claiming to be associated with the legit source. And, you fill you crucial data and get phished.
In mails, you can detect where the link is actually pointing to in real by just hovering mouse cursor over those embedded links.
2.Website Forgery: It’s a type of attack technique in which the hacker makes or replicates a reputed and legitimate website, by similar-looking domain names, etc. hosted on a free hosting service. Now, they ask users for filling in sensitive information.
Or, sometimes there is a use of some Java-script to spoof the address bar also or by hiding original bar and putting a fake image of that legit URL.
An attacker can also potentially use flaws in a trusted website’s own scripts against the victim. Where the SSL and other security certificates seem to be legit but actually this kind of website is created for these kinds of purposes. Sometimes a hacker infects the trusted sources as well, so that when a user visits a website and they allow some popup, the malware present on them gets installed or though caching stays in your PC.
3.Covert Redirect: These are phishing technique that makes a link appearing to be from legit sources then redirects the victim to an infected website.
4.Social Engineering: The use of social engineering can be by engaging the people on social media to click on some unexpected content for some reason for a reward. Or, Masquerading. Like a link points to a particular game on social media or anywhere and then it asks you to sign in with your Google account or Facebook account.
5.Filter Evasion: Sometimes on some scammers try to fool and prevent getting into sight of anti-phishing and other blockers and filters. Some make use of images instead of texts. Although, some OCR(Optical Character Reader) based tools are still able to detect hidden texts in images. To avoid it some also use adobe flash player, etc.
Now is a video for which I had promised at the beginning. The video shows a phishing mail came to our Official mail ID of Electroinvention. And, how I have detected that is it legit or not, and how to be safe.
So I hope now you know what are different types of phishing and types of phishing techniques. Also, now we know how can one scam and fool people and how to detect these things and stay protected.
I hope you guys liked this post and please comment below on how you feel about this article or if you have any questions.
Thank You.


Muchas gracias. ?Como puedo iniciar sesion?
ABHISHEK-HAXOR
Haha! Thanks for visiting and I am not hacker😂
👍
Thanks for visiting.
Babu bhaiya… joke apart, the article is awesome and very informative in-depth… Keep going…
Hello Shubham, Thanks for visiting, and glad you liked it.
Gokuro sama
Thanks for visiting and welcome.